In today's digital age, businesses heavily rely on their computer systems and networks to store and process critical data. The server room, a data center or computer room, is crucial in housing the servers and networking equipment that power these operations. Given the importance of these assets, it is essential to establish a secure server room environment and implement robust monitoring systems to ensure optimal performance, prevent unauthorized access, and safeguard against potential threats. This blog will delve into the details of monitoring mission-critical environments and outline the key steps to secure your server room effectively.
Importance of a Secure Server Room Environment
A server room houses vital equipment, including servers, routers, switches, and storage devices, which are the backbone of an organization's IT infrastructure. Here are some reasons why establishing a secure server room environment is of paramount importance:
- Data Protection: A secure server room helps protect sensitive data from unauthorized access, physical damage, and theft. Data breaches can have severe consequences, including financial loss, reputation damage, and legal liabilities.
- Business Continuity: Server rooms play a critical role in ensuring business continuity. By implementing robust security measures, you can minimize the risk of downtime caused by equipment failure, security breaches, or environmental hazards.
- Compliance with Regulations: Depending on the industry, businesses may be subject to various compliance regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Maintaining a secure server room environment can help meet these regulatory requirements.
- Disaster Recovery: In a disaster, such as a fire or natural calamity, a secure server room equipped with backup systems and redundant infrastructure can ensure data recovery and minimize downtime.
Key Steps to Secure Your Server Room Environment
Physical Access Controls
- Restricted Entry: Limit access to the server room to authorized personnel only. To prevent unauthorized entry, implement access control mechanisms, such as keycards, biometric scanners, or PIN codes.
- Surveillance Systems: Install CCTV cameras and monitor the server room 24/7. This provides real-time visibility and deters potential intruders.
- Security Alarms: Install security alarms to detect unauthorized access attempts or tampering. These alarms can alert security personnel and trigger appropriate actions.
- Visitor Logs: Maintain a logbook to record details of all individuals entering and exiting the server room. This helps track access and identify any potential security breaches.
Environmental Monitoring
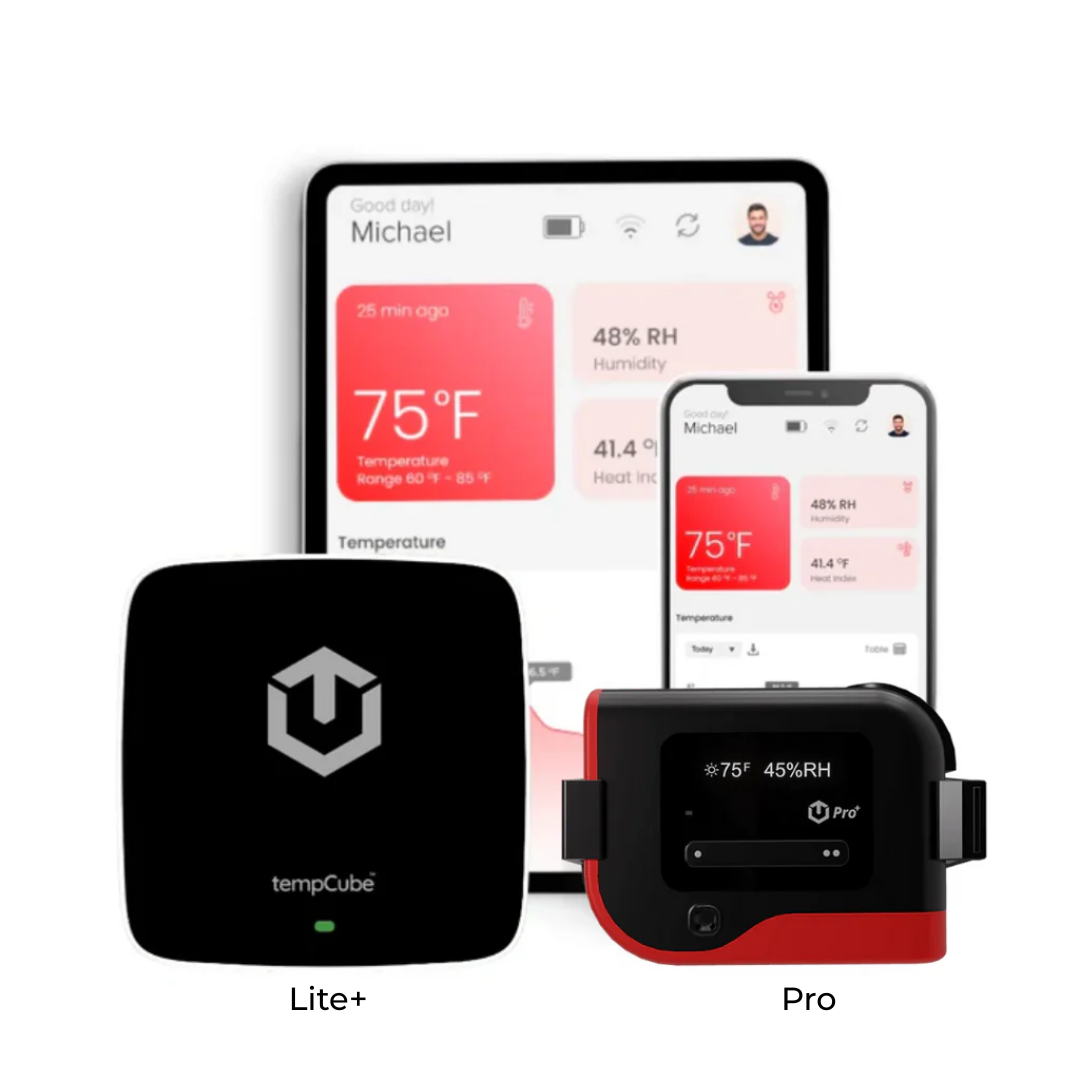
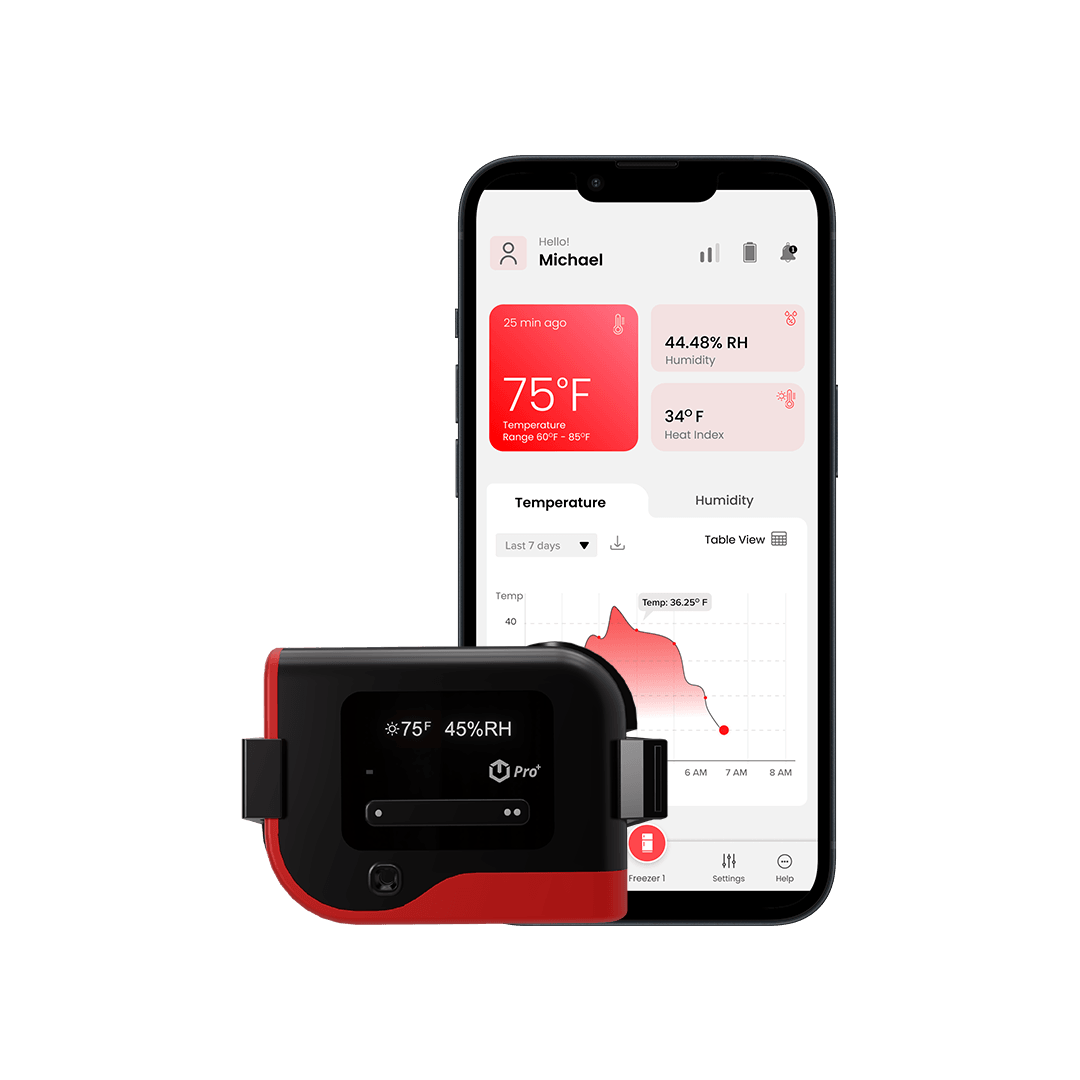
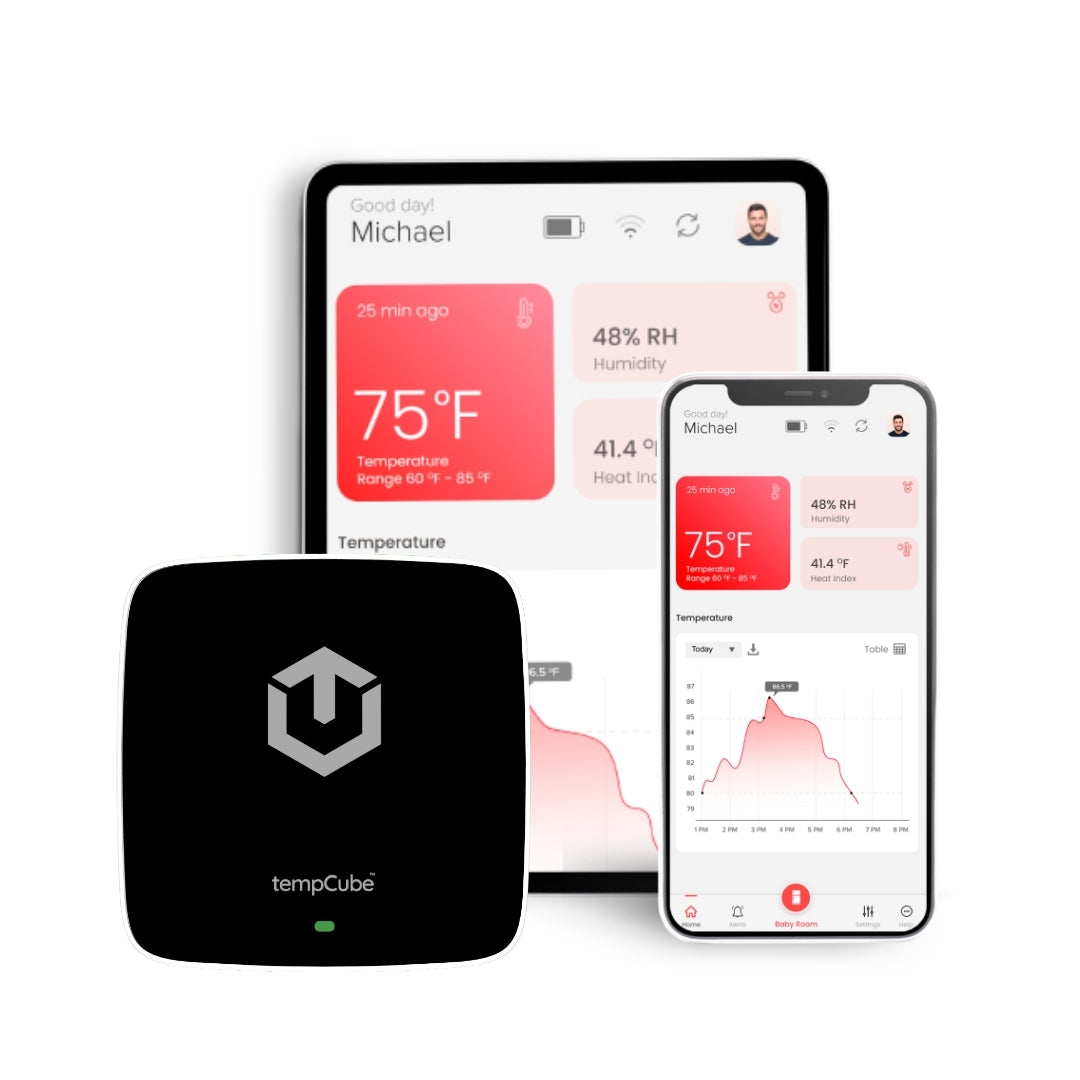
- Temperature and Humidity: Implement sensors to monitor temperature and humidity levels within the server room. Extreme conditions can damage equipment and affect performance. Set up alerts to notify administrators in case of deviations from acceptable ranges.
- Fire Detection and Suppression: Install smoke detectors and fire suppression systems, such as sprinklers or clean agent systems, to promptly detect and mitigate fire hazards.
- Water Leakage Detection: Deploy sensors to identify potential leaks or flooding. These sensors can help prevent water damage to critical equipment.
- Power Monitoring: Monitor power consumption and fluctuations to ensure a stable and uninterrupted power supply. Implement uninterruptible power supply (UPS) systems and backup generators to prevent downtime during power outages.
Network Security
- Firewall Protection: Deploy firewalls to protect the server room's network from unauthorized access and malicious threats. Configure firewall rules to allow only necessary traffic.
- Intrusion Detection and Prevention Systems (IDPS): Implement IDPS solutions to detect and prevent network intrusions, malware, and other cyber threats. Regularly update these systems with the latest threat intelligence.
- Network Segmentation: Segment the server room network into isolated zones to limit the potential impact of a security breach. This prevents unauthorized lateral movement within the web.
- Regular Vulnerability Assessments: Perform periodic vulnerability assessments and penetration testing to identify and address security weaknesses or loopholes.
Equipment Monitoring
- Server Monitoring: Utilize server monitoring tools to track the health and performance of servers. Monitor parameters such as CPU usage, disk space, and memory utilization to identify and proactively address potential issues.
- Network Device Monitoring: Monitor switches, routers, and other networking devices to ensure optimal performance, identify bottlenecks, and detect suspicious activities.
- Environmental Monitoring Systems (EMS): Implement EMS solutions that monitor environmental conditions, such as temperature, humidity, and airflow. These systems provide early warnings of potential equipment failures or environmental hazards.
Certainly! Here are some frequently asked questions (FAQs) related to securing a server room environment:
What is a server room?
A server room is a dedicated space within an organization where servers, networking equipment, and other critical IT infrastructure are housed. It is the central hub for managing and storing data, applications, and services.
Why is securing a server room important?
Securing a server room is crucial for protecting sensitive data, ensuring business continuity, complying with regulations, and minimizing the risk of unauthorized access, physical damage, or environmental hazards.
What are some physical access control measures for a server room?
Physical access control measures include restricted entry, such as keycards, biometric scanners, or PIN codes, surveillance systems (CCTV cameras), security alarms, and visitor logs to monitor and control access to the server room.
Conclusion
Establishing a secure server room environment is crucial for protecting mission-critical assets and ensuring the uninterrupted operation of businesses. Organizations can mitigate risks, safeguard sensitive data, and minimize downtime by implementing robust physical access controls, environmental monitoring systems, network security measures, and equipment monitoring solutions. In addition, regular monitoring, maintenance, and adherence to best practices in server room security are essential to adapt to evolving threats and maintain a secure infrastructure. Investing in protecting your server room environment will pave the way for a resilient and reliable IT infrastructure that can support your business's growth and success.